In July 2020, a hacker accessed Twitter’s internal tools to seize 130 high-profile Twitter accounts—like Elon Musk, Bill Gates, Barack Obama, and Jeff Bezos—to carry out a “double your bitcoin” scam.
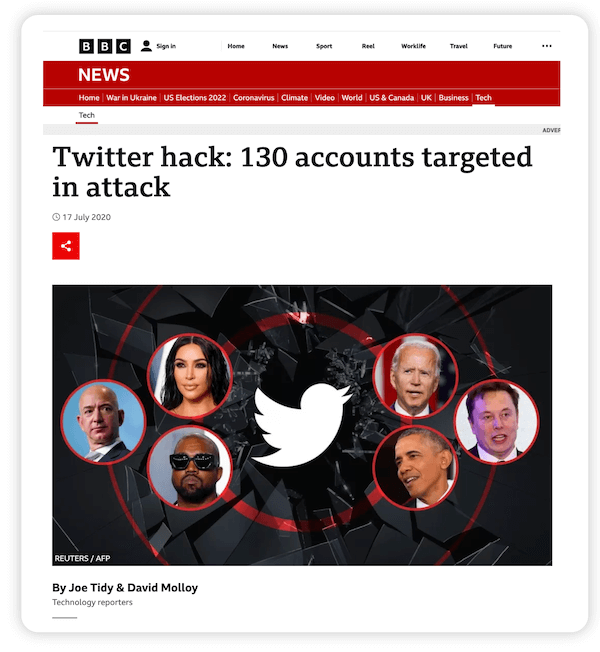
Thousands of Twitter users fell for it, and in just a few hours, the hacker stole over $118,000 worth of bitcoin. Since that time, thousands of organizations have been breached, from large multinationals like Apple and Facebook to universities, hotels, hospitals, government departments, and even churches and fundraising websites.
The fact is, any organization that collects, processes, or stores customer data is at risk of a breach—including yours. That’s why you must act now to protect this data. This article will show you how.
Table of contents
- The importance of data privacy
- Data privacy regulations & standards to know
- The biggest threats to data privacy & data security
- 10 best practices to protect your customer data
The importance of data privacy
Data privacy measures and controls have three main goals: To protect the information’s confidentiality and integrity, to build trust with customers, and to comply with data privacy laws. Failure to implement these controls can lead to a breach which can have serious consequences for both individuals and organizations.
Impact on individuals
Individuals whose data is stolen may become victims of identity theft or fraud. The hackers may use the stolen data to impersonate the victim and open lines of credit, apply for loans, etc.
The loss of sensitive or private data may also cause the victim to face humiliation, discrimination, financial losses, or psychological damage. In serious cases, their health, life, or family may be threatened.
Impact on organizations
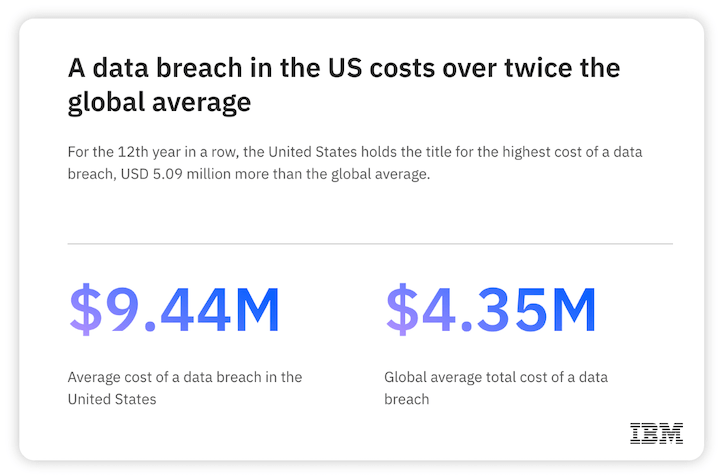
Data breaches hurt organizations as well, especially financially. According to IBM, the average cost of a breach has gone up to $4.35 million in 2022. Breach costs can include attackers’ ransom demands, plus “cleanup costs” related to breach remediation and forensic investigations. Regulatory fines and lawsuits may also add to the cost.
A breach can also damage the company’s reputation, customer perception, and stock prices. It may lose its customers’ trust and struggle to meet its contractual obligations, which could affect its business relationships and profits.
Data privacy regulations & standards to know
Following a spate of data breaches in recent years, many governments have implemented data privacy laws. These laws regulate how consumer data is collected, processed, stored, and discarded by organizations. They are meant to protect consumer data privacy and safeguard consumers from the damaging impact of data breaches.
GDPR
The GDPR applies to any company operating in any country that collects the information of EU residents. It governs how companies collect, use, transmit, and secure this data. Organizations that fail to comply with the law may be fined $20+ million or 4% of total global turnover.
U.S. data privacy laws
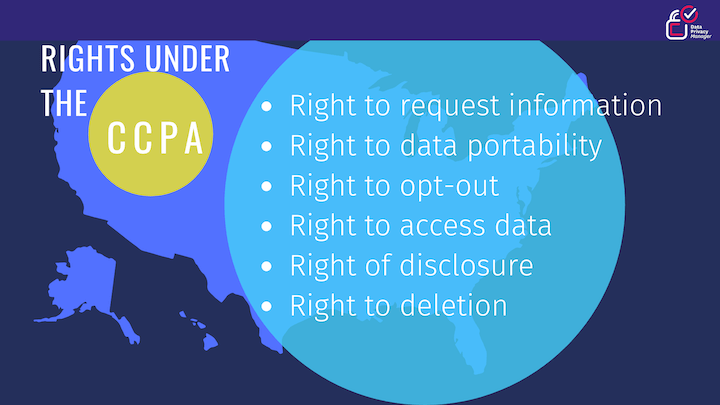
The USA does not have a single federal data privacy law. Instead, numerous sector- or state-specific laws govern how organizations collect, process, or use consumer data. For example, the Health Insurance Portability and Accounting Act (HIPAA) aims to maintain the privacy of protected health information (PHI). Similarly, the California Consumer Privacy Act (CCPA) controls how entities can collect the personal information of California residents.
Industry-specific privacy standards
Some industry bodies have developed privacy standards applicable to organizations in certain industries. One example is the PCI-DSS, which applies to all merchants worldwide who collect consumers’ credit card information. Although the standard is not enforced by any government, merchants must adhere to it due to their contractual relationship with the credit card company. The goal is to ensure that businesses implement the necessary safeguards to protect cardholder data and prevent credit card fraud.
Within the tech and advertising industry, we’ve seen a number of changes in recent years in the name of privacy. For example, Google reducing visibility into the search terms report and Facebook mandating Aggregated Event Measurement.
🔷 Free guide: 10 Privacy-Friendly Facebook Targeting Strategies
The biggest threats to data privacy & security
Data privacy is about controlling how the data is collected, shared, and used, while data security is concerned with protecting data from external attackers and malicious insiders. Despite these differences, there are several overlaps between these ideas. Additionally, there are many threats that can affect both data privacy and security.
Phishing scams
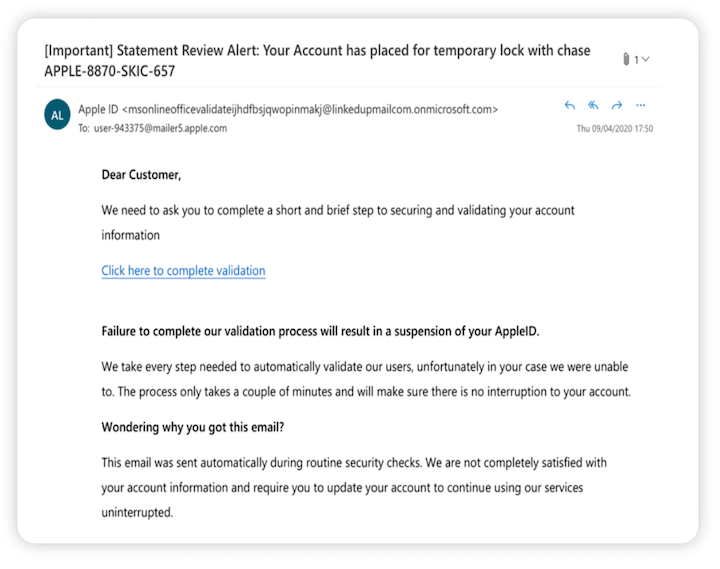
In a phishing scam, the attacker sends out emails that appear to come from a trusted source. The email may contain a malicious link or a malicious attachment. When a user clicks on the link, they will be taken to a website where they will be asked to provide their private information.
The attacker then steals this information, resulting in a breach. If the user opens the attachment, the attacker could compromise their device. They may also gain access to other resources on the enterprise network and cause widespread damage. Therefore, it’s important to ensure you’re investing in the right anti-phishing solution for your business.
Malware and ransomware
Malware and ransomware are huge threats to data security and privacy. In a ransomware attack, an attacker infects corporate devices with malware that encrypts the system and locks out the user. In exchange for the decryption key, the criminal demands a hefty ransom from the organization. Many ransomware strains can spread throughout the network and exfiltrate huge amounts of data.
Insider threats
Insider threats are another serious threat to data privacy. Since 2020, the frequency of insider incidents has increased by 44%, and the cost per incident has increased to $15.38 million.
Some threats come from malicious or compromised insiders such as employees or third-party vendors. Others come from non-malicious or careless insiders with poor cybersecurity hygiene. For example, a user may share their password with a colleague while another may store sensitive data in a public folder. Such mistakes can result in accidental data leaks or exposures.
Software vulnerabilities
Security vulnerabilities in devices and applications open the door to cybercriminals. Many attackers exploit these vulnerabilities to attack organizations and exfiltrate or compromise customer data.
10 best practices to protect customer data privacy
Here are ten ways to protect your valuable customer data from cyberattackers and hackers.
1. Know what data you are collecting
You can only protect data if you know what it is and where it is stored. Understand what kind of data you collect from customers, how it is used, and who is using it. You should also know how sensitive the data is, where it is stored, and when it is shared.
Conduct a data audit to identify data throughout the enterprise. Then categorize each data type according to sensitivity, use case, and need for accessibility. Finally, prepare a data inventory to understand what data needs to be protected and which compliance laws apply to your organization.
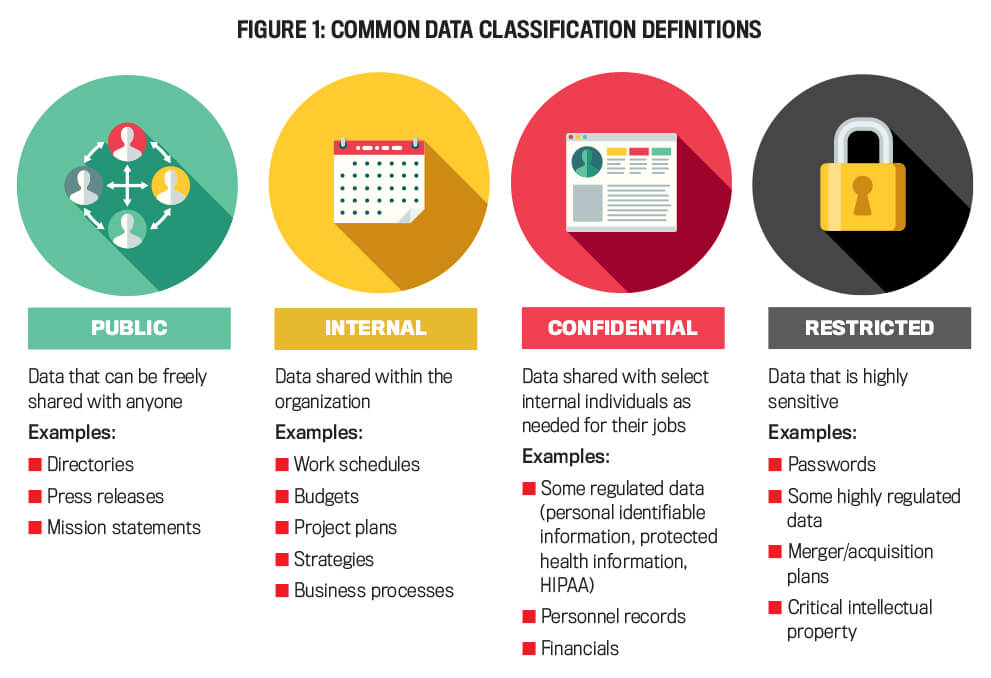
Here are some classifications of data to consider:
- Public data: Press releases, mission statements, directory listing information.
- Internal data: Work schedules, budgets, project plans, business processes, strategies, marketing data.
- Confidential data: Personal information, protected health information, personnel records, financials.
- Restricted data: Passwords, merger/acquisition plans, intellectual property.
2. Only collect essential information
You can minimize the potential damage of a data breach by collecting a limited amount of personal data. Collect only the private or sensitive data you need for your business to meet certain goals, for example, to improve customer experiences and retention.
To evaluate which data is essential, conduct periodic data audits. Then assess whether you actually need that data. If not, stop collecting it. This way, you can decrease the possibility of losses if a breach happens.
3. Create and publish a transparent data usage and privacy policy
Define and implement a clear data privacy policy and communicate it to all stakeholders. The policy should specify who is allowed to access the data and how. It should also clearly state how the data should and shouldn’t be used.
Also, publish a privacy policy for customers on your business website. The policy should state how your company collects, stores, uses, and protects customer data. If you make changes to the policy, make sure to keep customers informed.
4. Encrypt all sensitive user data
Unencrypted, poorly-stored data gives hackers a reason to attack the organization. Encrypt all your data, both in transit and at rest. Use 256-key bit length encryption to secure data in emails and file-level encryption to protect data on systems and servers.
In addition, take regular data backups and store the backups in a secure location. This way, even if you are the target of a cyberattack like ransomware, you can still access the data. Moreover, you won’t have to pay the ransom.

5. Protect against phishing scams
To reduce the risk of loss due to phishing attacks, implement email spam filters throughout the organization. Also update all devices with antivirus and anti-malware software that updates automatically to deal with emerging threats and continually protect data.
People play an important role in minimizing the impact of phishing attacks. Encourage employees to report any email scams they encounter to the appropriate person or department.
6. Update all software
Hackers take advantage of security vulnerabilities in devices and software to attack organizations and compromise customer data. Software vendors usually release patches after they detect vulnerabilities in their products. Implement these patches to bring your software up to date and protect your customer data.
7. Implement multi-factor authentication
Multi-factor authentication (MFA) provides more robust protection for enterprise accounts and data. MFA requires an additional authentication factor, not just a password. So, even if a hacker steals an authorized user’s password, they will still need the second factor to log into an enterprise account. Usually, this factor remains in the authorized user’s control, so it’s difficult for a hacker to compromise or steal it.

8. Train people about cybersecurity practices
Cybersecurity education is essential to eliminate people-related weaknesses in cybersecurity. Educate your employees on cybersecurity best practices. Train them to recognize the signs of a phishing attack and how to avoid social engineering scams.
Explain the importance of strong passwords and MFA. Also, show them why they should not use public Wi-Fi networks for work and always adhere to the organization’s security and privacy policies.
9. Limit access to data
Limiting access to data on a need-to-know basis minimizes internal threats to the data. Whenever possible, implement the principle of least privilege (PoLP), so users can only access or edit the data they need for their role. Manage access levels and permissions with identity and access management (IAM) tools.
10. Implement a comprehensive data protection infrastructure
To secure customer data and avoid breaches, you need a comprehensive security infrastructure with all these tools:
- Antivirus and anti-malware software
- Anti-adware and anti-spyware software
- Next-generation web firewall
- Pop-up blockers
- Endpoint detection and response (EDR) tools
- Vulnerability scanner
- Password manager
- MFA
Set aside a budget for these tools. They will help protect your organization from data breaches, and you will recover your investment fairly quickly.
Keep your business, customers & data safe
The number and frequency of data breaches have increased considerably in recent years. The last five years have been especially bad, with hackers targeting a number of high-profile organizations and affecting millions of people.
Fortunately, all is not lost. You do have some control over the data you collect and use. More importantly, you can secure this data and keep it from falling into the wrong hands. By employing the ideas and best practices shared here, you can reduce the risks to your company and customers.
- Know what data you are collecting
- Only collect essential information
- Create and publish a transparent data usage and privacy policy
- Encrypt all sensitive user data
- Protect against phishing scams
- Update all software
- Implement multi-factor authentication
- Train people about cybersecurity practices
- Limit access to data
- Implement a comprehensive data protection infrastructure
About the author
Irina Maltseva is a Growth Lead at Aura and a Founder at ONSAAS. For the last seven years, she has been helping SaaS companies to grow their revenue with inbound marketing. At her previous company, Hunter, Irina helped 3M marketers to build business connections that matter. Now, at Aura, Irina is working on her mission to create a safer internet for everyone. To get in touch, follow her on LinkedIn.
The post Customer Data Privacy: 10 Non-Negotiable Best Practices to Protect Your Business appeared first on WordStream.
* This article was originally published here
No comments:
Post a Comment